“If you spend more time on coffee than on IT security, you’ll be hacked. What’s more, you deserve to be hacked.”
— Richard Clarke, White House Cybersecurity Advisor, 1992-2003
Security has always been a paramount concern for organisations, especially in the current dynamics, where the threats of cybersecurity, physical breaches, and unauthorized access have been bombarding businesses of all sizes.
In fact, the threat is so big that in Q2 of 2024, organizations have experienced an average of 1,636 cyberattacks per week, which represents a 30% year-over-year increase.
And, this is why to protect your business from unauthorized intrusion, a proper access control system comes into play to foster a secure working environment. So, this read will be diving deep into the various types of access control system that are available along with their application to find your best match.
Let’s start!
1. Discretionary Access Control (DAC)
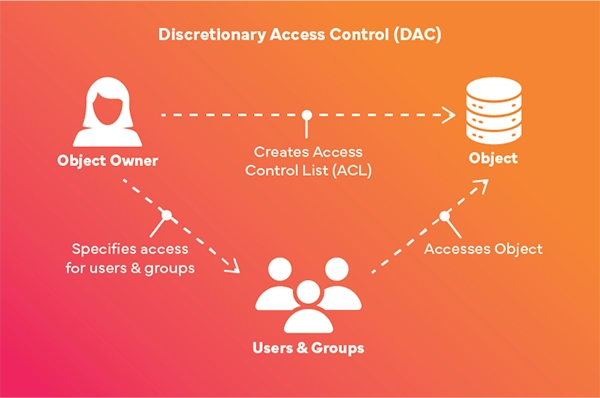
Discretionary Access Control is a system in which the power to give a permit lies in the hands of the owner/the highest authority. It makes it more flexible for business owners but at the same time, it can be less secure since the permission can readily be shared among users.
Key Features:
- Access based on user: The owner assigns permissions.
- Flexible for small businesses or offices.
- For environments that are less security sensitive.
Use: DAC is mostly located in coworking spaces or little workplaces that require adaptable entry to various regions.
2. Mandatory Access Control (MAC)
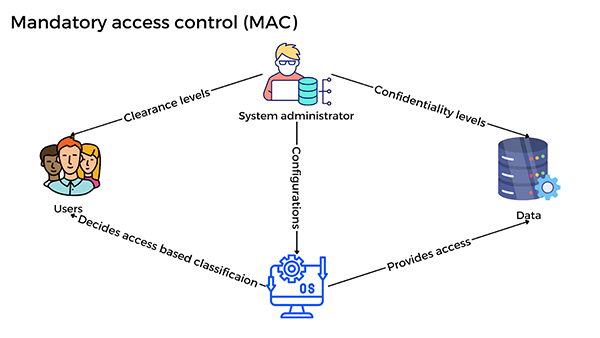
Mandatory Access Control (Macro Access Control) is stringent in nature. In this system, the terms are determined and regulated by a central authority.
Since the user has no power to modify their own permissions on the server, it is very well suited for highly secure places like military or government facilities.
Key Features:
- It is a central authority that enforces strict rules.
- Most secure, therefore good for delicate locations.
- Their permissions cannot be changed by users.
Use: MAC is extensively employed in government buildings, research labs, and high-security industrial sectors including defence and banking.
3. Role-Based Access Control (RBAC)
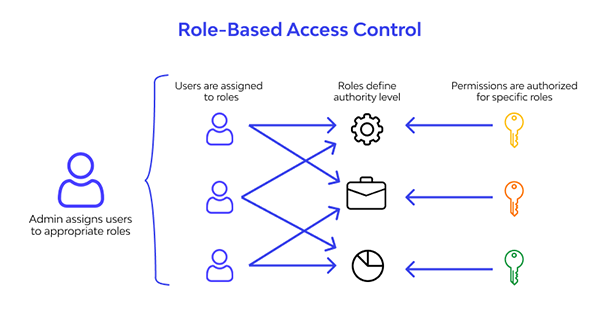
One of the most often utilized structures is Role-Based Access Control (RBAC), where supply is combined depending on the title ascribed to a user within a company. The method uses task assignments to regulate entry, thus making it easier for organizations to manage who gets in and out.
Key Features:
- Grants rights depending on a user’s role.
- This means that in large organizations, this simplifies entry.
- Most appropriate for multi-tiered corporate workspaces.
Use: In various countries like India, the use of RBAC is predominantly observed in IT companies, educational institutions and health care facilities where access to different regions depends on job functions.
4. Biometric Access Control

Using Biometrics such as fingerprints, face recognition or eye scans, biometric access control systems allow entry. These are incomparably safe systems because they are based on biometric data which cannot be accurately copied. In India, these are gaining momentum, especially among establishments that have high levels of security or those that rely heavily on technological devices.
Key Features:
- Using fingerprints, retinas or facial recognition.
- Enhanced security through the use of individual biological characteristics.
- Can be connected to other systems managing access.
Use: Sensitive data protection is a number one priority in various fields like technology and banking, as well as in corporate environments that employ biometric systems.
5. Card-Based Access Control

Card-based access systems are one of the most used systems. Cards are given to employees or authorized people that give them the right to enter secured regions by swiping or tapping their card on the provided reader.
These systems are both cost-effective and easy to implement, making them popular in offices, hospitals, and universities.
Key Features:
- Having an ID card is how employees enter their offices.
- This method is affordable and can be expanded.
- Moreover, it can be used together with other security measures like a personal identification number or biometric verification.
Use: Enterprises, educational organizations and hospitals usually employ card systems because they are compatible with the security devices already in place and are very simple to use.
6. Proximity Access Control

The technology on which proximity access control systems are based is RFID (Radio Frequency Identification). Users have a card or a key fob with a chip embedded in it, and they gain entrance to the system if the card is near the reader.
These systems are also user-friendly since they do not require physical contact with the reader, thereby preventing wear and tear.
Key Features:
- RFID technology is utilized for contactless access.
- Ideal for areas with a lot of foot traffic.
- Decreases the likelihood of card deterioration caused by usage.
Use: Near-feeds utilize technology that has become increasingly adopted by many airports, metro hubs and retail arenas within various Indian states where easy transitions and less crowding are of utmost importance.
Do You Know?
The Access Control Market in India was valued at $160.20 million in 2021 and is expected to reach $313.11 million by 2030.
7. Mobile-Based Access Control

In this, Smartphones give people entry to certain spaces controlled by phone-based systems. Employees or authorized individuals can unlock gates or restricted areas remotely using mobile applications or Bluetooth technology; hence, this approach is more recent and convenient in terms of accessibility.
Key Features:
- Uses smartphones for access.
- It can be combined with other automated building systems.
- It is most suited for remote or flexible job settings.
Use: Mobile-based systems are being increasingly utilized in technology companies, smart buildings and residential complexes in India, emphasizing on flexibility and modern infrastructure.
8. Cloud-Based Access Control

Cloud-based access control systems provide a centralized way to manage one’s access across different locations. Since this is managed via cloud technology, administrators can set up or monitor access from a distance. It is suitable for large or multi-location companies because it offers scalability, flexibility, and less hardware expenses.
Key Features:
- Centralised, cloud-based management.
- Monitoring is done in real time.
- Every type of company can use it.
Use: Cloud systems are widely accepted by companies having various branches in various locations of India because they provide the ability to manage them from a distance and offer immediate entry regulation.
9. Intercom Access Control

Intercoms not only grant doors for people to enter but do it with minimal effort to communicate messages of access. This can take place through voice call instructions or by use of video communication, where guests are allowed entrance through these means. In homes, offices, and other secure workplaces, these systems are commonly used.
Key Features:
- Access control is based on communication.
- It can be combined with both video systems.
- Visitor management is made easier.
Use: Visitor access monitoring and control is achieved through intercom systems, which are used largely in homes and workplaces.
10. Keypad Access Control

To access keypad systems, one needs to input a PIN or code. They are cost-friendly and easy to install, but may need frequent changes in the entry code to ensure safety.
Key Features:
- Access using PIN Code.
- Easy to use and easy on pockets.
- Regular updates on codes are required.
Use: In those places where sophisticated protection is not of primary concern, keypad technologies are commonly used such as in tiny workspaces, storage areas and residential estates.
CONCLUSION:
The most important thing for the protection of your business or home is a good access control system. All types of these systems have their own advantages and cater for varying needs and security levels.
In a dynamic and fast-evolving market like India investing in a strong and scalable entry control system can enhance security, streamline operations and bring peace of mind. Understanding the different options available will help you make an informed decision concerning the protection of your assets as well as operations.
- 1. Discretionary Access Control (DAC)
- 2. Mandatory Access Control (MAC)
- 3. Role-Based Access Control (RBAC)
- 4. Biometric Access Control
- 5. Card-Based Access Control
- 6. Proximity Access Control
- 7. Mobile-Based Access Control
- 8. Cloud-Based Access Control
- 9. Intercom Access Control
- 10. Keypad Access Control
- CONCLUSION:




